Top Guidelines Of Health and Wellness
The insights introduced With this report are dependant on an extensive study by pros with varied cybersecurity designations across fourteen industries, with over 50% boasting ten years or even more in the sphere.
Observe coupled with Yahoo Sports below for the many highlights, Are living updates and analysis from Clark’s preseason debut.
Just months soon after its initial launch, visionOS 2 provides effective spatial computing encounters to Apple Vision Pro, together with new ways for users to produce spatial images with the pictures by now within their library, intuitive hand gestures to easily entry essential information at a glance, and new characteristics for Mac Virtual Screen, Travel Mode, and Guest Person.
” In this post, I’ll be unveiling the method by which these men and women develop into adept at exploiting the vulnerabilities of Computer system units and why being familiar with this process might help within the fight versus cybercrime. Keep reading to discover the interior workings with the hacker’s brain.
The most significant hack in historical past is considered the info breach in opposition to Yahoo! The 2013 assault compromised all around three billion individuals, and the corporate exposed that each Yahoo! customer was influenced by it.
A regime software update induced cascading chaos Friday that has engulfed global businesses from airports and banking companies to retail and law enforcement.
Treasury, IRS situation up-to-date steering on expected bare minimum distributions from IRAs, other retirement programs; typically retains proposed principles Treasury, IRS concern updated guidance on demanded least distributions from IRAs, other retirement options; normally retains proposed policies
Validate cybercontrols—Specially emerging ones—technically to make certain your readiness for evolving threats and systems.
The stakes of our political decisions haven't been increased, but with new headlines every single hour it could be difficult to different the signal in the sounds. On Politically Sound, we’re going to have a move again check here and consider the huge picture. We’ll explain the...
On top of that, remaining inside legal and moral boundaries when hacking can't be overstated as it's significantly important on this planet of cybersecurity.
The remarkable increase in cyber-assaults globally, particularly ransomware incidents, indicators an urgent will need for strong cyber stability frameworks. Organizations have to prioritize cyber safety, adopting custom made strategies to effectively beat the evolving threat landscape.
Consequently, fashionable-day hacking will involve far more than just an indignant child of their Bed room. It's really a multibillion-dollar industry with particularly advanced and profitable techniques.
CNN also offers protection of big events including the Olympics plus the Super Bowl, as well as weather updates from meteorologist Chad Myers. The station's programming is meant to attract a wide range of listeners, including Those people keen on remaining informed about the most up-to-date developments in the world of news and latest activities.
Other frequent hacker styles contain blue hat hackers, which happen to be amateur hackers who perform destructive functions like revenge attacks, crimson hat hackers, who seek out black hat hackers to circumvent their attacks, and eco-friendly hat hackers, who want to find out about and observe hacking approaches on hacking forums.
 Angus T. Jones Then & Now!
Angus T. Jones Then & Now!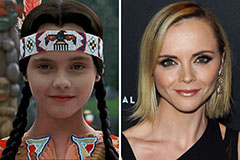 Christina Ricci Then & Now!
Christina Ricci Then & Now!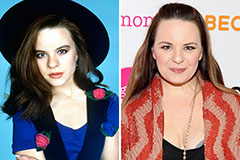 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Mackenzie Rosman Then & Now!
Mackenzie Rosman Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now!